It’s All in the Applications
pfSense Plus is a powerful product with a rich set of add-in packages that allow customers to tailor it to almost any edge or cloud secure networking need. We have conveniently grouped its capability set into the five most commonly needed applications.

What is Attack Prevention?
Simply stated, attack prevention is stopping malicious actors from carrying out exploits and threats against your network infrastructure and proprietary information. Multiple layers of network security are required to do this effectively - at the network edge, within the network, at the device level, in the cloud, etc.
The types of attack prevention that make sense at the network edge include:
- Intrusion detection and prevention
- Network traffic analysis
- Deep packet inspection
- Application blocking
pfSense Plus offers a suite of highly-regarded add-in packages to effectively address attack prevention

IDS/IPS
Snort-based Packet Analyzer
Layer 7 Application Detection
Multiple Rules, Sources, & Categories
Emerging Threats Database
IP Blacklist Database
Pre-Set Rule Profiles
Per Interface Config.
False Positive Alert Suppression
Deep Packet Inspection (DPI)
Application Blocking
Attack Prevention Features
IDS/IPS
Intrusion Detection Systems (IDS) analyze network traffic for signatures that match known cyberattacks. Intrusion Prevention Systems (IPS) analyzes packets as well, but can also stop the packet from being delivered, helping to halt the attack.
More information can be found in our documentation.
Snort-based Packet Analyzer
Snort is a packet sniffer that monitors network traffic in real time, scrutinizing each packet closely to detect a dangerous payload or suspicious anomalies.
More information can be found in our documentation.
Layer 7 Application Detection
Layer 7, the OSI (Open System Interconnection) Model application layer, supports application and end-user processes, such as HTTP and SMTP. Attacks at this layer present a security challenge as malicious code can masquerade as valid client requests and normal application data.
More information can be found in our documentation.
Multiple Rules, Sources, and Categories
Depending on choices around performance, security risk tolerance, and actual business applications in use, there are many ways to configure an IDS/IPS. pfSense Plus software supports the use of multiple sources of rules for both Snort and Suricata. Additionally, each of those packages have multiple categories for rules as well, including floating rules, interface group rules, and interface rules.
More information can be found in our documentation.
Emerging Threats Database
An IDS/IPS solution can be configured to simply log detected network events, or both log and block them. This is performed through the use of detection signatures, called rules. Rules can be custom created by the user, or any of several pre-packaged rule sets can be enabled and downloaded. Pre-packaged rulesets offer added detection / protection against emerging threats in the wild.
More information can be found in our documentation.
IP Blacklist Database
IP blacklisting filters out illegitimate or malicious IP addresses from accessing your networks. pfBlocker is a pfSense Plus software package that allows you to add IP block list and country block lists.
More information can be found in our documentation.
Pre-Set Rule Profiles
pfSense Plus software is equipped with a number of automatically added firewall rules. Examples include anti-lockout, anti-spoofing, block private networks, block Bogon networks, IPsec protocol use and port access, default deny rule, etc.
Per-Interface Configuration
pfSense Plus software allows each LAN or WAN interface to be independently configured with firewall rules and other per-interface functionality.
False Positive Alert Suppression
Each IDS/IPS security admin must ultimately decide their own alert volume tolerance, as only you know the type of traffic that is normal on your network. pfSense Plus software enables you to select specific ruleset and alerting policies on a per interface basis, as well as offering detailed guidance about how to eliminate noisy false positives.
Deep Packet Inspection (DPI)
Deep Packet Inspection (DPI) enables security analysts to capture and evaluate full packet header and payload information to identify protocol compliance, spam, virus, intrusion, and other anomalous or malicious traffic. Snort, Suricata, and NTOPNG packages each support DPI capabilities.
More information can be found in our documentation here (NTOPNG), here (Snort) and here (Suricata).
Application blocking
pfSense Plus software leverages Snort and OpenAppID to detect, monitor and manage application usage on your network.
Who Needs Attack Prevention?

Home Users
If your home network has externally facing servers, e.g., a hosted website, or if you need to access your home network when you are not at home), an IDS/IPS is probably unnecessary.
The stateful firewall functionality, core to pfSense Plus is probably sufficient, i.e., traffic flowing inbound will not be allowed in unless explicitly allowed to, but outbound traffic will be allowed to return - even without an explicit rule.

Remote Workers
Certainly as a result of the global pandemic - where many employees transitioned from their offices to remote work - cybercriminals began developing new tactics to take advantage of an expanded attack surface. In most cases, however, increased attack prevention measures are still best applied at the “business termination” end of remote worker connections - where network security personnel can monitor for unusual outbound network activity, irregular account activity, geographic anomalies, spikes in network activity, etc. can be monitored and analyzed across all remote workers. So as with home users, the stateful firewall functionality core to pfSense Plus is probably sufficient.

Business, Education, Government
All business, education and government agency locations are well-advised to take advantage of all aspects of attack prevention: IDS/IPS, network traffic analysis, deep packet inspection, application blocking, etc.

Service Providers
Service providers operate sophisticated networks and should certainly leverage all forms of attack prevention including IDS/IPS, network traffic analysis, deep packet inspection, application blocking, etc., both for their own IT infrastructure, and end customers if operating as an MSSP.
Where Should Attack Prevention Be Deployed?
Attack prevention solutions are commonly placed at the network edge, or in the case of cloud-based applications, at the Virtual Private Instance (VPI) edge. Consideration should always be given to the depth and breadth of rule sets in order to keep traffic performance to acceptable levels.
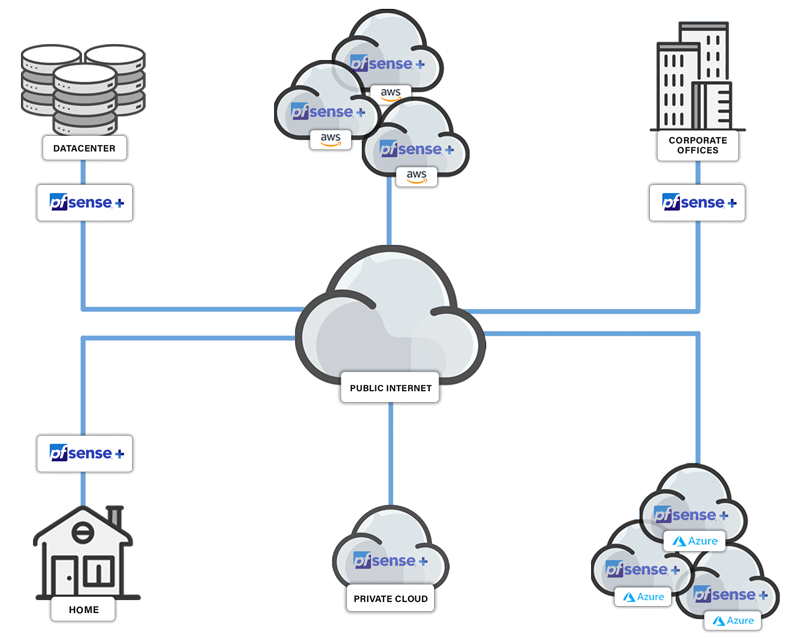
What Makes pfSense Plus a Great Attack Prevention Solution?
Easy to use
- User-friendly web interface makes configuration and administration easy - even for users with limited networking knowledge
- Observe key operating metrics like network utilization, CPU load and disk space usage with built-in Zabbix monitoring
- Comprehensive documentation and a wealth of YouTube videos for specific assistance
All the features you need
- Snort and Suricata IDS/IPS package options
- Packet analysis, Layer 7 application detection, emerging threat management, alert suppression, deep packet inspection, application blocking and more
- Not just an attack prevention solution, but also a full firewall, VPN and router solution
Proven reliability and resilience
- Deployed on hundreds of thousands of Netgate appliances, 3rd party appliances, virtual machines, and cloud instances in every vertical on every continent
- Highly lauded by customers for reliability and stability
- Configurable as a High Availability (HA) cluster for business assurance
Excellent overall solution value
- Unbeatable combination of feature set (attack prevention, firewall, router, and VPN), price-performance and ease of use
- Proven dependability for consumers, businesses and service providers
- World-class, highly-rated support options for business assurance
-01.png?width=926&height=181&name=Netgate%20Logo%20PMS%20(horizontal)-01.png)
%201.png?width=302&name=Netgate%20Logo%20PMS%20(horizontal)%201.png)
