It’s All in the Applications
pfSense Plus is a powerful product with a rich set of add-in packages that allow customers to tailor it to almost any edge or cloud secure networking need. We have conveniently grouped its capability set into the five most commonly needed applications.

What is a firewall?
A firewall creates a barrier between your network, whether home or office - and the Internet, providing a safeguard for your computers, servers, printer, etc. from the outside world. It does this by applying security politics (rules) that determine what traffic is allowed in or out of your network.
There are four basic types of firewalls:
- Packet Filter Firewalls - controls network access by analyzing incoming and outgoing traffic at the packet level, allowing or blocking packets with policies around IP addresses, packet type, port number, etc. Packet filter firewalls cannot stop application layer or spoofing attacks.
- Stateful Packet Inspection (SPI) Firewalls - examine traffic streams from end to end and block unauthorized traffic by analyzing packet headers and the state of the packets. SPI firewalls are more secure than basic packet filtering firewalls.
- Proxy Server Firewalls (also referred to as application level gateways) - mask your IP address and limit traffic, thus protecting your network resources by filtering messages at the application layer. Proxy server firewalls are the most secure type of firewall.
- Next Generation Firewall (NGFW) - addresses all of the above and adds features like application awareness and control, integrated intrusion detection/prevention, and threat intelligence feeds.
pfSense Plus covers all four bases.

Stateful Packet Inspection (SPI)
GeoIP Blocking
Anti-Spoofing
Captive Portal Guest Network
Time-Based Rules
Connection Limits
NAT Mapping (Inbound / Outbound)
Firewall Features
Stateful Packet Inspection (SPI)
A stateful firewall is a network-based firewall that individually tracks sessions of network connections traversing it. Stateful packet inspection, also referred to as dynamic packet filtering, is a security feature used to invoke fine-grained security policies. pfSense Plus software does this by default, and can be configured to block traffic based on policy matches. Alternatively, one can just inspect and not block traffic, by adding pass rules for all traffic on each interface from any/to any as desired.
More information can be found in our documentation.
GeoIP Blocking
GeoIP filtering can block web traffic from entire countries, one mechanism for stopping hackers from attacking your business. Network connections are blocked based on geographic location (information gathered from IP addresses) which can then be used to filter and prevent outgoing and incoming connections to and from your business.
pfSense Plus software by default implicitly blocks all unsolicited inbound traffic to the WAN interface.
More information can be found in our documentation under pfBlockerNG.
Anti-Spoofing
Anti spoofing detects packets with false addresses which leads to increased security.
More information can be found in our documentation under Anti-spoofing Rules.
Captive Portal Guest Network
A captive portal is a web page accessed with a web browser that is displayed to newly connected users of a Wi-Fi or wired network before they are granted broader access to network resources.
More information can be found in our documentation.
Time-Based Rules
Time based rules allow firewall rules to activate during specified days and/or time ranges. Time based rules function the same as any other rule, except they are effectively not present in the ruleset outside of their scheduled times.
More information can be found in our documentation.
Connection Limits
A firewall connection limit policy allows or denies traffic based on a matching tuple: source address, destination address, and service; and connection count, which enables detection of anomalous connection requests.
More information can be found in our documentation.
NAT Mapping (Inbound / Outbound)
Network address translation (NAT) is a method of mapping an IP address space into another by modifying network address information in the IP header of packets while they are in transit across a traffic routing device.
More information can be found in our documentation.
Who Needs a Firewall?

Home Users
If you only have a single computer at home that connects to the Internet, you probably don’t need a network firewall. A PC/Mac on-board firewall is fine. But, if you have two devices or more, a network firewall is important. A typical home these days could have multiple computers, printers, door alarms, cameras, kitchen appliances, gaming consoles, etc. - all connecting to the Internet, and all potential targets of savvy, persistent attackers. Your personal privacy and security is at stake.

Remote Workers
The 2020 pandemic has forever changed the landscape of remote work. While certainly not new, COVID-19 changed many organizations from 5% work from home to 95% work from home. This opens an entirely new population of targets for hackers looking to infiltrate an organization’s IT infrastructure, data and intellectual property through remote worker compromise.

Business, Education, Government
Businesses of any size, K-12 and higher education institutions, and local, state and federal government agencies all have physical locations and IT infrastructure that need firewall protection. This is never more true than today with a constantly evolving business landscape, increasing workforce dispersion, and increasingly sophisticated and motivated hacker population.

Service Providers
Whether in support of protecting their own IT infrastructure, or as a key element of security services extended to their consumer and business customers, service providers continue to depend upon firewalls as a core element of secure networking solutions.
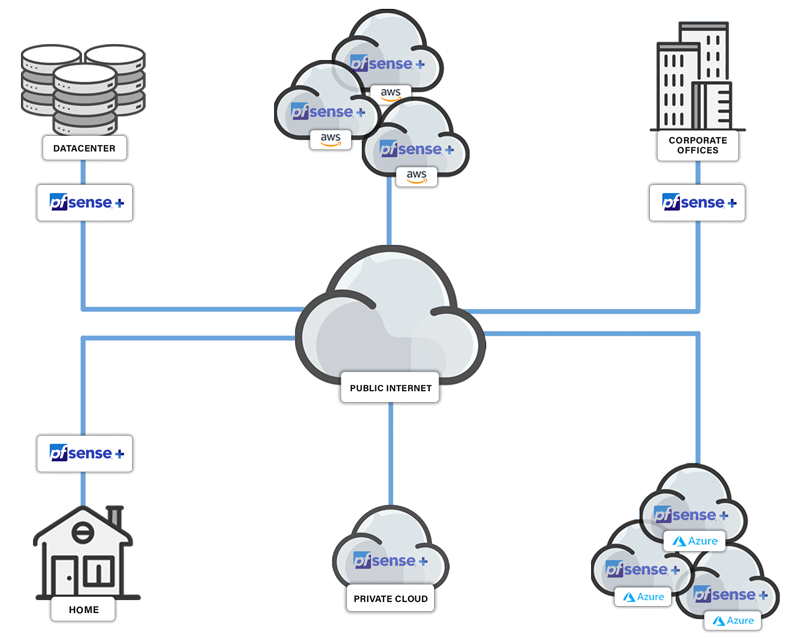
Where Should Firewalls Be Deployed?
A simple rule is wherever you have an Internet connection, you likely need a firewall. Common deployment locations include the network edge where each of the following connect to the Internet:
- Home
- Office
- Data Center
- Public Cloud - owned and operated by a third-party cloud service provider
- Private Cloud - physically located at your organization’s on-site datacenter, or hosted by a third-party service provider
To serve each location (whether physical or virtual) and customer deployment preference, pfSense Plus is available on a turnkey Netgate appliance, a virtual machine instance, and on select public cloud service provider marketplaces.
What Makes pfSense Plus a Great Firewall?
Easy to use
- User-friendly web interface makes configuration and administration easy - even for users with limited networking knowledge
- Observe key operating metrics like network utilization, CPU load and disk space usage with built-in Zabbix monitoring
- Comprehensive documentation and a wealth of YouTube videos for specific assistance
All the features you need
- Covers all the bases - packet filter, stateful packet inspection, proxy server, and next generation firewall feature sets
- Package manager enables feature customization to meet exacting needs
- Not just a firewall, also a full VPN and router solution
Proven reliability and resilience
- Deployed on hundreds of thousands of Netgate appliances, 3rd party appliances, virtual machines, and cloud instances in every vertical on every continent
- Highly lauded by customers for reliability and stability
- Configurable as a High Availability (HA) cluster for business assurance
Excellent overall solution value
- Unbeatable combination of feature set (firewall, router, and VPN), price-performance and ease of use
- Proven dependability for consumers, businesses and service providers
- World-class, highly-rated support options for business assurance
-01.png?width=926&height=181&name=Netgate%20Logo%20PMS%20(horizontal)-01.png)
%201.png?width=302&name=Netgate%20Logo%20PMS%20(horizontal)%201.png)
